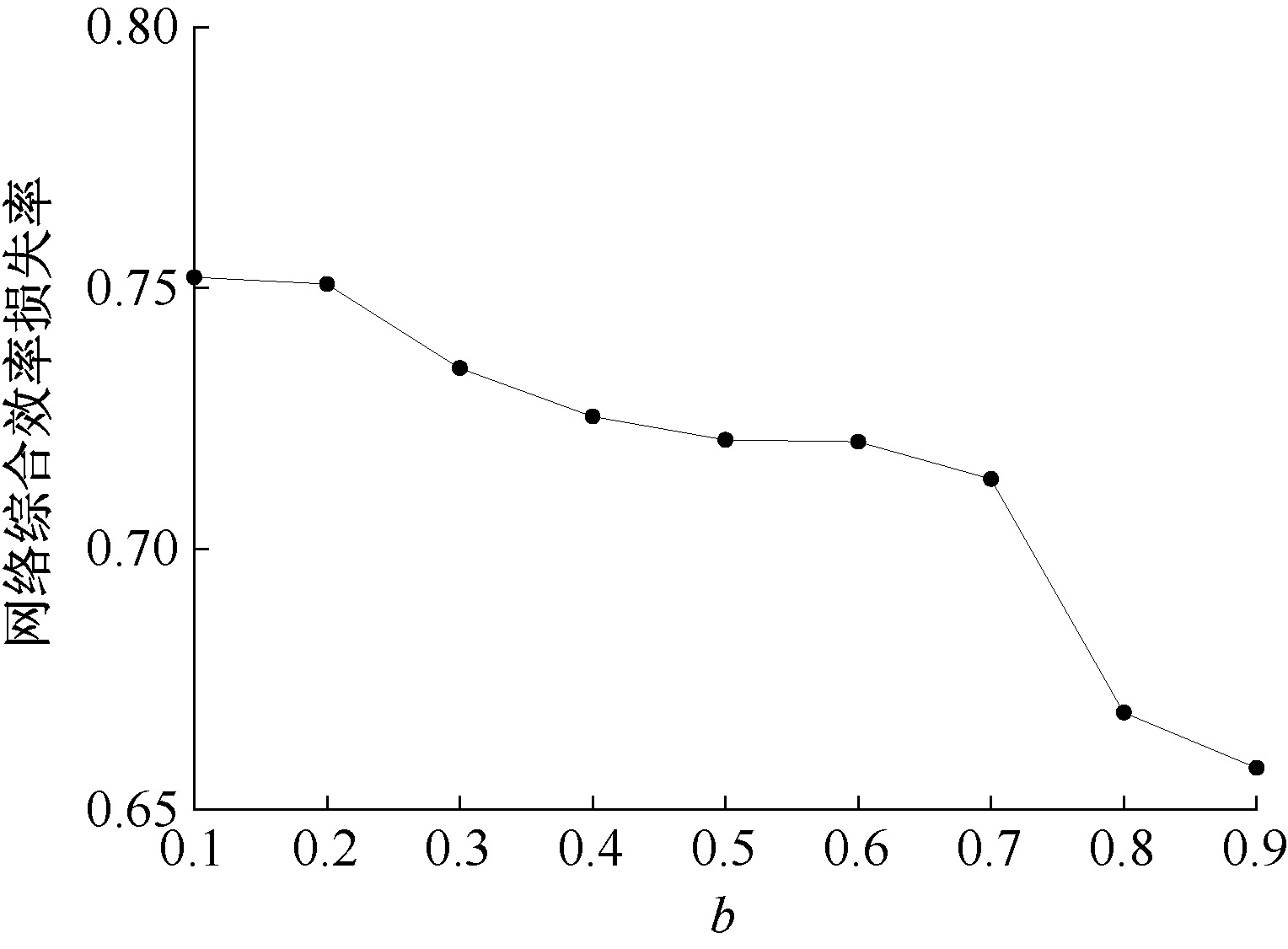
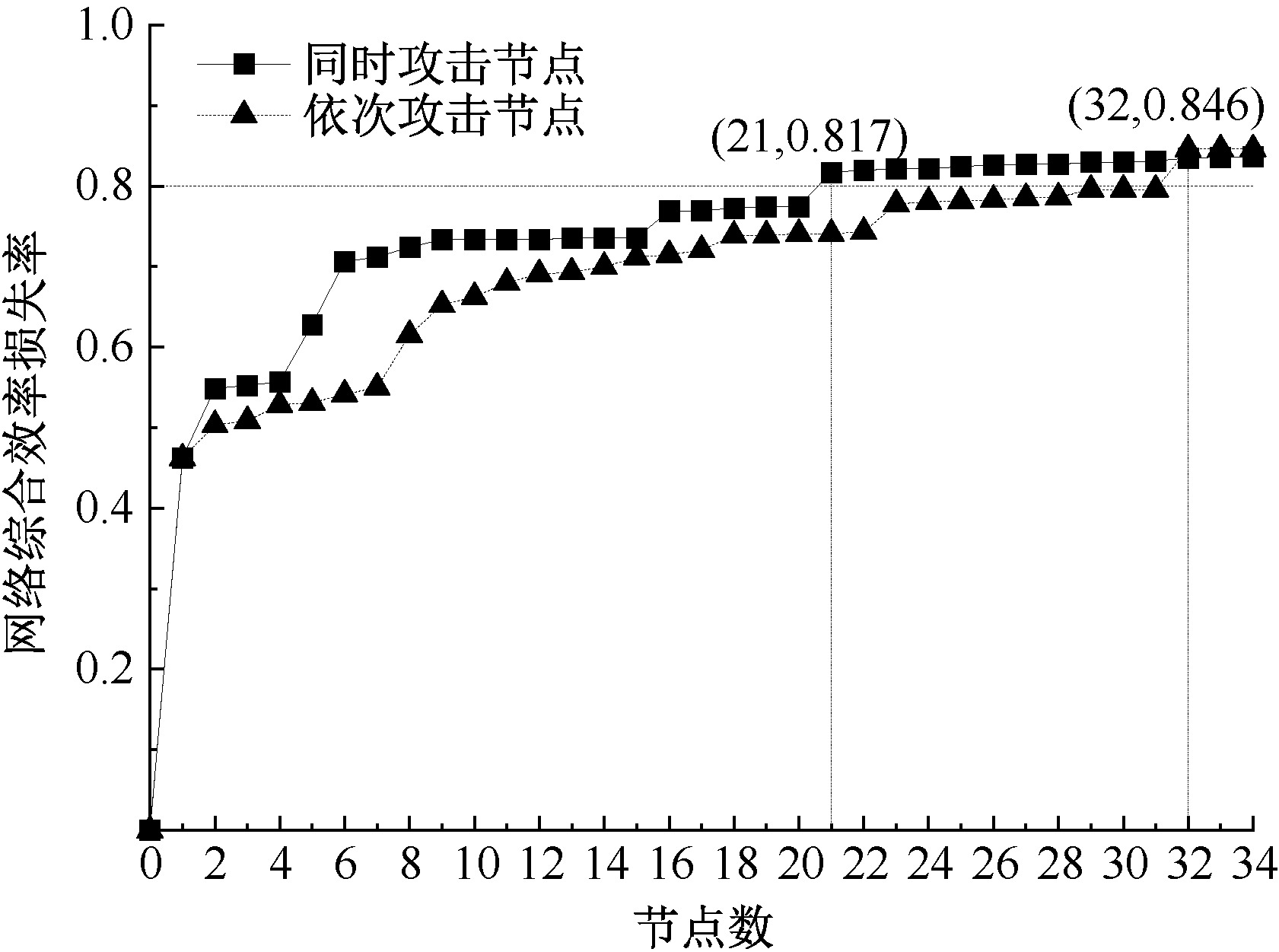
| [1] |
侯秀芳, 冯晨, 左超, 等. 2022年中国内地城市轨道交通线路概况[J]. 都市快轨交通, 2023, 36(1): 9-13.
|
|
HOU Xiufang, FENG Chen, ZUO Chao, et al. Statistical analysis of urban rail transit in Chinese mainland in 2022[J]. Urban Rapid Rail Transit, 2023, 36(1): 9-13.
|
| [2] |
ZHANG Shuyang, LO H K, NG K F, et al. Metro system disruption management and substitute bus service: a systematic review and future directions[J]. Transport Reviews, 2021, 41(2): 230-251.
doi: 10.1080/01441647.2020.1834468
|
| [3] |
邓旭东, 王雪, 徐文平, 等. 城市地铁网络脆弱性对比分析[J]. 中国安全科学学报, 2017, 27(3): 152-156.
doi: 10.16265/j.cnki.issn1003-3033.2017.03.027
|
|
WANG Xudong, WANG Xue, XU Wenping, et al. Comparative analysis of vulnerability of urban metro network[J]. China Safety Science Journal, 2017, 27(3): 152-156.
doi: 10.16265/j.cnki.issn1003-3033.2017.03.027
|
| [4] |
SUN Lishan, HUANG Yuchen, CHEN Yanyan, et al. Vulnerability assessment of urban rail transit based on multi-static weighted method in Beijing, China[J]. Transportation Research Part A: Policy and Practice, 2018, 108: 12-24.
doi: 10.1016/j.tra.2017.12.008
|
| [5] |
ZHANG Jianhua, WANG Ziqi, WANG Shuliang, et al. Vulnerability assessments of urban rail transit networks based on redundant recovery[J]. Sustainability, 2020, 12(14):DOI: 10.3390/su12145756.
|
| [6] |
邓勇亮, 李启明, 陆莹, 等. 城市地铁网络系统的物理脆弱性研究[J]. 中国安全科学学报, 2013, 23(10): 76-81.
|
|
DENG Yongliang, LI Qiming, LU Ying, et al. Analysis of urban metro network system physical vulnerability[J]. China Safety Science Journal, 2013, 23(10): 76-81.
|
| [7] |
路庆昌, 崔欣, 徐标, 等. 公交接驳场景下轨道交通网络脆弱性研究[J]. 中国安全科学学报, 2021, 31(8): 141-146.
doi: 10.16265/j.cnki.issn1003-3033.2021.08.020
|
|
LU Qingchang, CUI Xin, XU Biao, et al. Vulnerability research of rail transit network under bus connection scenarios[J]. China Safety Science Journal, 2021, 31(8): 141-146.
doi: 10.16265/j.cnki.issn1003-3033.2021.08.020
|
| [8] |
CHEN Hongyu, ZHANG Limao, LIU Qiong, et al. Simulation-based vulnerability assessment in transit systems with cascade failures[J]. Journal of Cleaner Production, 2021, 295:DOI: 10.1016/j.jclepro.2021.126441.
|
| [9] |
万丹, 郭倩, 邓良凯, 等. 城市轨道交通网络脆弱性对比研究[J]. 城市轨道交通研究, 2021, 24(1): 60-64.
|
|
WAN Dan, GUO Qian, DENG Liangkai, et al. Comparative study on vulnerability of urban rail transit network[J]. Urban Mass Transit, 2021, 24(1): 60-64.
|
| [10] |
STARITA S, AMIDEO A E, SCAPARRA M P. Assessing urban rail transit systems vulnerability: metrics vs. interdiction models[C]. International Conference on Critical Information Infrastructures Security, 2017: 144-155.
|
| [11] |
齐小刚, 张碧雯, 刘立芳, 等. 复杂信息网络的弹性评估和优化方法研究[J]. 计算机科学与探索, 2018, 12(8): 1252-1262.
doi: 10.3778/j.issn.1673-9418.1706058
|
|
QI Xiaogang, ZHANG Biwen, LIU Lifang, et al. Evaluation and optimization of complex network resilience against attacks[J]. Journal of Frontiers of Computer Science and Technology, 2018, 12(8): 1252-1262.
|
| [12] |
王萌, 张建华, 邹培栋, 等. 南京城市轨道交通网络脆弱性分析[J]. 中国科技论文, 2017, 12(19): 2172-2175.
|
|
WANG Meng, ZHANG Jianhua, ZOU Peidong, et al. Vulnerability analysis of Nanjing urban rail transit network[J]. China Sciencepaper, 2017, 12(19): 2172-2175.
|
| [13] |
SHI Jiangang, WEN Shiping, ZHAO Xianbo, et al. Sustainable development of urban rail transit networks: a vulnerability perspective[J]. Sustainability, 2019, 11(5): DOI: 10.3390/su11051335.
|
| [14] |
薛锋, 何传磊, 黄倩. 成都地铁网络的关键节点识别方法及性能分析[J]. 中国安全科学学报, 2019, 29(1):93-99.
doi: 10.16265/j.cnki.issn1003-3033.2019.01.016
|
|
XUE Feng, HE Chuanlei, HUANG Qian. Identification of key nodes in Chengdu metro network and analysis of network performance[J]. China Safety Science Journal, 2019, 29(1):93-99.
doi: 10.16265/j.cnki.issn1003-3033.2019.01.016
|
| [15] |
HONG Chen, ZHANG Jun, DU Wenbo, et al. Cascading failures with local load redistribution in interdependent Watts-Strogatz networks[J]. International Journal of Modern Physics C, 2016, 27(11): DOI: 10.1142/S012918311650131X.
|
| [16] |
李从东, 李文博, 曹策俊, 等. 面向级联故障的相依网络鲁棒性分析[J]. 系统仿真学报, 2019, 31(3): 538-548.
doi: 10.16182/j.issn1004731x.joss.17-0217
|
|
LI Congdong, LI Wenbo, CAO Cejun, et al. Robustness analysis of interdependent networks for cascading failure[J]. Journal of System Simulation, 2019, 31(3): 538-548.
doi: 10.16182/j.issn1004731x.joss.17-0217
|
| [17] |
PENG Xingzhao, YAO Hong, DU Jun, et al. Invulnerability of scale-free network against critical node failures based on a renewed cascading failure model[J]. Physica A: Statistical Mechanics and its Applications, 2015, 421: 69-77.
doi: 10.1016/j.physa.2014.11.024
|
| [18] |
黄婷婷, 朱海燕, 杨聚芬. 基于前景理论的轨道交通乘客路径选择模型[J]. 都市快轨交通, 2019, 32(2): 59-63.
|
|
HUANG Tingting, ZHU Haiyan, YANG Jufen. The route choice model of urban rail traveler based on prospect theory[J]. Urban Rapid Rail Transit, 2019, 32(2): 59-63.
|
| [19] |
蔡鉴明, 邓薇. 长沙地铁网络复杂特性与级联失效鲁棒性分析[J]. 铁道科学与工程学报, 2019, 16(6): 1587-1596.
|
|
CAI Jianming, DENG Wei. Complex characteristics of Changsha metro network and robustness analysis of cascading failures[J]. Journal of Railway Science and Engineering, 2019, 16(6): 1587-1596.
|
| [20] |
张慧慧, 陈峰, 吴奇兵. 北京地铁进出站设施通行瓶颈问题定量分析[J]. 都市快轨交通, 2009, 22(3): 20-23.
|
|
ZHANG Huihui, CHEN Feng, WU Qibing. Quantitative analysis on the bottleneck of Beijing Subway access facilities[J]. Urban Rapid Rail Transit, 2009, 22(3): 20-23.
|
| [21] |
杨景峰, 朱大鹏, 赵瑞琳. 城轨网络站点重要度评估与级联失效抗毁性分析[J]. 中国安全科学学报, 2022, 32(8): 161-167.
doi: 10.16265/j.cnki.issn1003-3033.2022.08.1148
|
|
YANG Jingfeng, ZHU Dapeng, ZHAO Ruilin. Evaluation of station importance and cascading failure resistance analysis of urban rail transit network[J]. China Safety Science Journal, 2022, 32(8): 161-167.
doi: 10.16265/j.cnki.issn1003-3033.2022.08.1148
|
| [22] |
SUN Daniel Jian. GUAN Shituo. Measuring vulnerability of urban metro network from line operation perspective[J]. Transportation Research Part A: Policy and Practice, 2016, 94: 348-359.
doi: 10.1016/j.tra.2016.09.024
|
| [23] |
魏润斌, 贾顺平, 毛保华, 等. 考虑满载率均衡的城市轨道交通直通运营开行方案优化[J]. 哈尔滨工业大学学报, 2023, 55(3): 68-77.
|
|
WEI Runbin, JIA Shunping, MAO Baohua, et al. Train planning optimization for through operation of urban rail transit considering load balance[J]. Journal of Harbin Institute of Technology, 2023, 55(3): 68-77.
|
| [24] |
VARGA B, TETTAMANTI T, KULCSÁR B. Optimally combined headway and timetable reliable public transport system[J]. Transportation Research Part C: Emerging Technologies, 2018, 92: 1-26.
doi: 10.1016/j.trc.2018.04.016
|
| [25] |
MA Fei, SHI Wenjing, YUEN K F, et al. Exploring the robustness of public transportation for sustainable cities: a double-layered network perspective[J]. Journal of Cleaner Production, 2020, 265: DOI: 10.1016/j.jclepro.2020.121747.
|