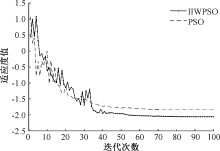
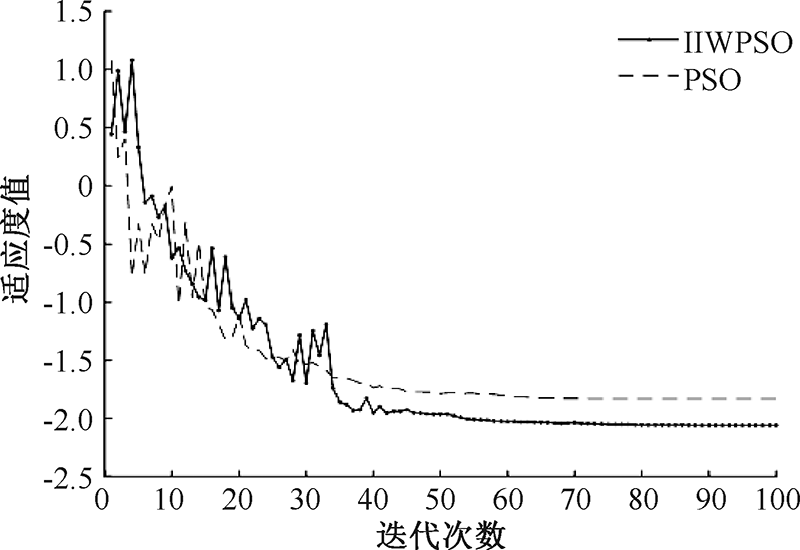
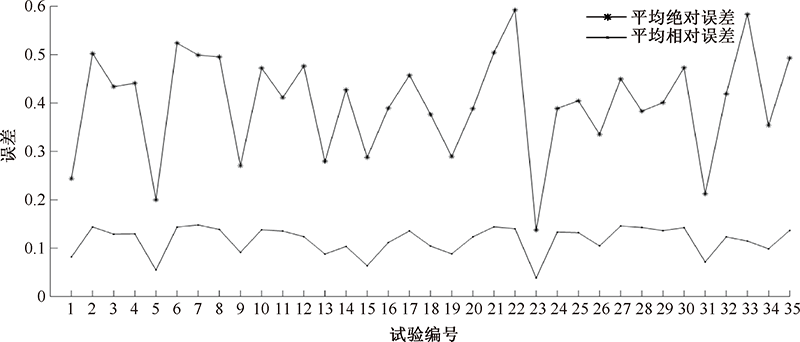
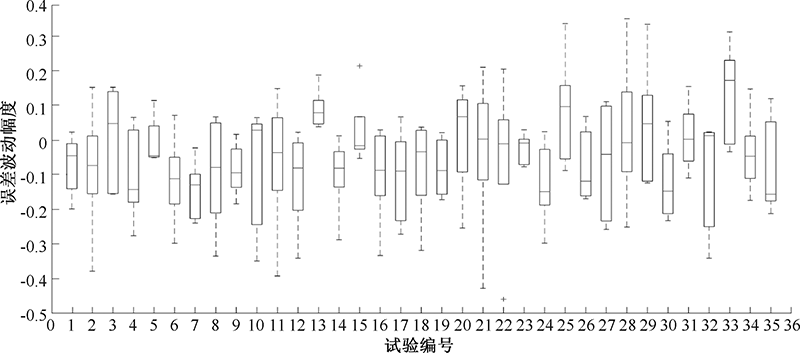
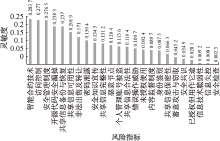
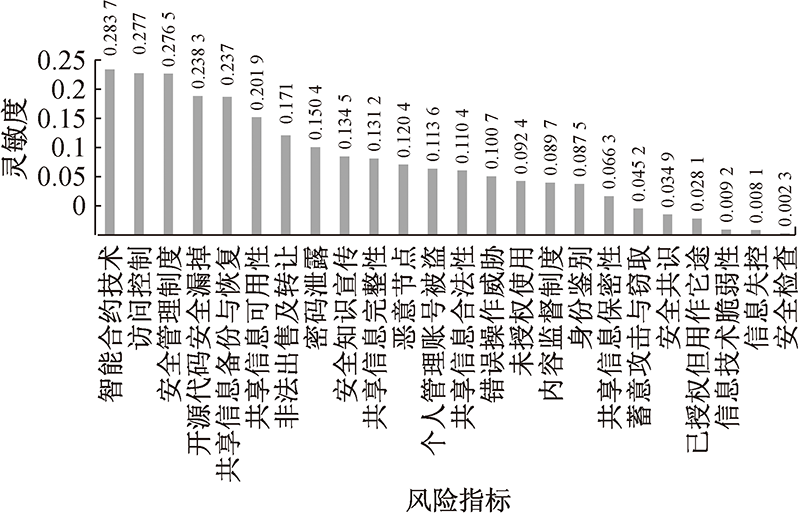
| [1] |
石娟, 郑鹏, 常丁懿. 大数据环境下的城市公共安全治理:区块链技术赋能[J]. 中国安全科学学报, 2021, 31(2):24-32.
doi: 10.16265/j.cnki.issn 1003-3033.2021.02.004
|
|
SHI Juan, ZHENG Peng, CHANG Dingyi. Urban public security governance under big data environment: blockchain technology empowerment[J]. China Safety Science Journal, 2021, 31(2):24-32.
doi: 10.16265/j.cnki.issn 1003-3033.2021.02.004
|
| [2] |
曹策俊, 李从东, 王玉, 等. 大数据时代城市公共安全风险演化与治理机制[J]. 中国安全科学学报, 2017, 27(7): 151-156.
doi: 10.16265/j.cnki.issn1003-3033.2017.07.027
|
|
CAO Cejun, LI Congdong, WANG Yu, et al. Evolution and governance mechanism of urban public safety risk in big data era[J]. China Safety Science Journal, 2017, 27(7): 151-156.
doi: 10.16265/j.cnki.issn1003-3033.2017.07.027
|
| [3] |
翟伟, 盛智平, 果希光, 等. 雄安新区工程监理区块链管理模式研究与应用[J]. 中国安全科学学报, 2021, 31(4):27-33.
doi: 10.16265/j.cnki.issn1003-3033.2021.04.004
|
|
ZHAI Wei, SHENG Zhiping, GUO Xiguang, et al. Research on engineering supervision blockchain management pattern in Xiong' an new area and its application[J]. China Safety Science Journal, 2021, 31(4):27-33.
doi: 10.16265/j.cnki.issn1003-3033.2021.04.004
|
| [4] |
郭祖华, 李扬波, 徐立新, 等. 面向云计算的网络安全风险预测模型的研究[J]. 计算机应用研究, 2015, 32(11):3421-3425.
|
|
GUO Zuhua, LI Yangbo, XU Lixin, et al. Research of network security risk prediction model based on cloud computing[J]. Application Research of Computers, 2015, 32(11):3421-3425.
|
| [5] |
向尚, 邹凯, 蒋知义, 等. 基于随机森林的智慧城市信息安全风险预测[J]. 中国管理科学, 2016, 24(增1):266-270.
|
|
XIANG Shang, ZOU Kai, JIANG Zhiyi, et al. Risk prediction of smart city information security based on random forest[J]. Chinese Journal of Management Science, 2016, 24(S1):266-270.
|
| [6] |
张艳丰, 王羽西, 邹凯, 等. 基于模糊DANP的智慧城市信息安全风险要素识别与管理策略研究[J]. 情报理论与实践, 2020, 43(10):144-150.
|
|
ZHANG Yanfeng, WANG Yuxi, ZOU Kai, et al. Research on the identification and management strategy of risk factors of smart city information security based on fuzzy DANP[J]. Information Studies:Theory & Application, 2020, 43(10):144-150.
|
| [7] |
FRANCHINA L, SOCAL A. Innovative predictive model for smart city security risk assessment[C]. 2020 43rd International Convention on Information, Communication and Electronic Technology (MIPRO), 2020: 1831-1836.
|
| [8] |
邹凯, 向尚, 张中青扬, 等. 智慧城市信息安全风险评估模型构建与实证研究[J]. 图书情报工作, 2016, 60(7):19-24.
doi: 10.13266/j.issn.0252-3116.2016.07.003
|
|
ZOU Kai, XIANG Shang, ZHANG Zhongqingyang, et al. Model construction and empirical study on smart city information security risk assessment[J]. Library and Information Service, 2016, 60(7):19-24.
|
| [9] |
毛子骏, 梅宏, 肖一鸣, 等. 基于贝叶斯网络的智慧城市信息安全风险评估研究[J]. 现代情报, 2020, 40(5):19-26,40.
|
|
MAO Zijun, MEI Hong, XIAO Yiming, et al. Risk assessment of smart city information security based on Bayesian network[J]. Journal of Modern Information, 2020, 40(5):19-26,40.
|
| [10] |
腾讯电脑管家. 2018上半年区块链安全报告[EB/OL]. [2020-05-23].
|
| [11] |
中国互联网金融协会区块链研究工作组. 中国区块链金融应用与发展研究报告[EB/OL]. [2020-04-14].
|