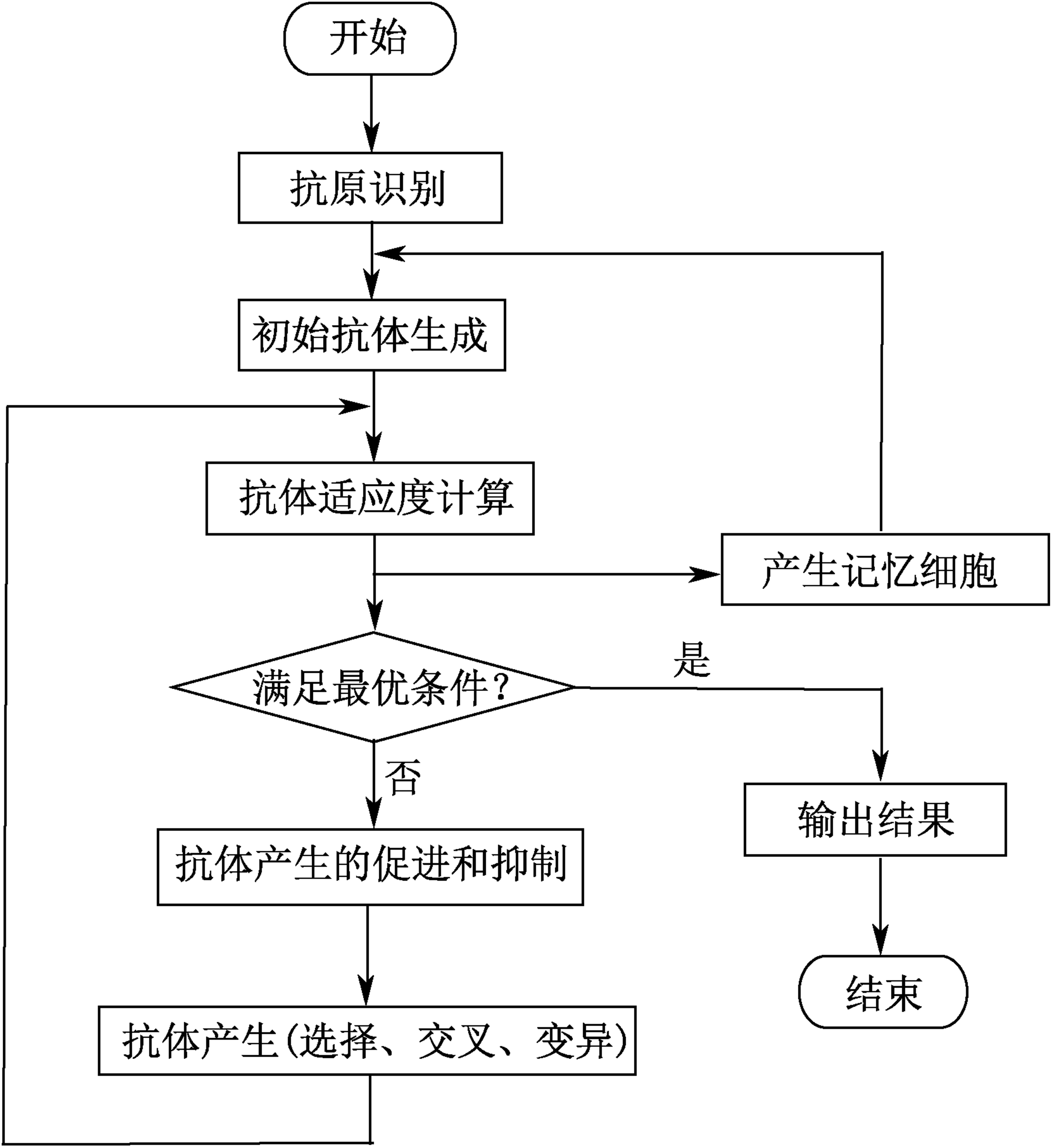
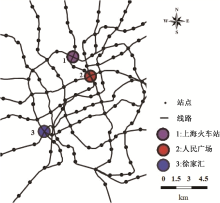
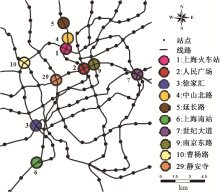
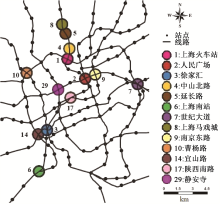
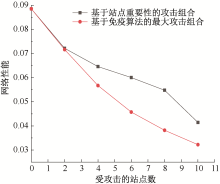
| [1] |
BERDICA K. An introduction to road vulnerability:what has been done, is done and should be done[J]. Transport Policy, 2002, 9(2): 117-127.
doi: 10.1016/S0967-070X(02)00011-2
|
| [2] |
LU Qingchang, ZHANG Lei, XU Pengcheng, et al. Modeling network vulnerability of urban rail transit under cascading failures: a coupled map lattices approach[J]. Reliability Engineering & System Safety, 2022, 221: DOI: 10.1016/j.ress.2022.108320.
doi: 10.1016/j.ress.2022.108320
|
| [3] |
叶青. 基于复杂网络理论的轨道交通网络脆弱性分析[J]. 中国安全科学学报, 2012, 22(2):122-126.
|
|
YE Qing. Vulnerability analysis of rail transit based on complex network theory[J]. China Safety Science Journal, 2012, 22(2): 122-126.
|
| [4] |
路庆昌, 崔欣, 徐标, 等. 公交接驳场景下轨道交通网络脆弱性研究[J]. 中国安全科学学报, 2021, 31(8): 141-146.
doi: 10.16265/j.cnki.issn1003-3033.2021.08.020
|
|
LU Qingchang, CUI Xin, XU Biao, et al. Vulnerability research of rail transit network under bus connection scenarios[J]. China Safety Science Journal, 2021, 31(8): 141-146.
doi: 10.16265/j.cnki.issn1003-3033.2021.08.020
|
| [5] |
LÓPEZ F, PÁEZ A, CARRASCO J, et al. Vulnerability of nodes under controlled network topology and flow autocorrelation conditions[J]. Journal of Transport Geography, 2017, 59: 77-87.
doi: 10.1016/j.jtrangeo.2017.02.002
|
| [6] |
MARTELLO M, WHITTLE A, KEENAN J, et al. Evaluation of climate change resilience for Boston's rail rapid transit network[J]. Transportation Research Part D: Transport and Environment, 2021, 97: DOI: 10.1016/j.trd.2021.102908.
doi: 10.1016/j.trd.2021.102908
|
| [7] |
RODRÍGUEZ-NÚÑEZ E, GARCÍA-PALOMARES J. Measuring the vulnerability of public transport networks[J]. Journal Transport Geography, 2014, 35: 50-63.
doi: 10.1016/j.jtrangeo.2014.01.008
|
| [8] |
薛锋, 何传磊, 黄倩. 成都地铁网络的关键节点识别方法及性能分析[J]. 中国安全科学学报, 2019, 29(1): 93-99.
doi: 10.16265/j.cnki.issn1003-3033.2019.01.016
|
|
XUE Feng, HE Chuanlei, HUANG Qian. Identification of key nodes in Chengdu metro network and analysis of network performance[J]. China Safety Science Journal, 2019, 29(1): 93-99.
doi: 10.16265/j.cnki.issn1003-3033.2019.01.016
|
| [9] |
万丹, 郭倩, 邓良凯, 等. 城市轨道交通网络脆弱性对比研究[J]. 城市轨道交通研究, 2021, 24(1):60-64.
|
|
WAN Dan, GUO Qian, DENG Liangkai, et al. Comparative study on vulnerability of urban rail transit network[J]. Urban Mass Transit, 2021, 24(1): 60-64.
|
| [10] |
肖明辉. 基于区域攻击的城市公共交通互补网络脆弱性分析[J]. 信息通信, 2018(8):1-5.
|
|
XIAO Minghui. The vulnerability analysis of urban complementary transit network under spatially localized failures[J]. Information and Communications, 2018(8):1-5.
|
| [11] |
崔欣, 路庆昌, 李建宇. 基于网络冗余性的城市轨道交通关键站点识别[J]. 中国安全科学学报, 2022, 32(12): 158-164.
doi: 10.16265/j.cnki.issn1003-3033.2022.12.0274
|
|
CUI Xin, LU Qingchang, LI Jianyu, et al. Key station identification of urban rail transit based on network redundancy[J]. China Safety Science Journal, 2022, 32(12): 158-164.
doi: 10.16265/j.cnki.issn1003-3033.2022.12.0274
|